Background and Behaviour
After migrating our virtual machines (VMs) from AAPT’s virtual datacentre (AAPT vDC) to Telstra’s Cloud Infrastructure (Telstra.Cloud Shared) we have observed, that after a period of inactivity, our RDP sessions to our Windows VMs keep getting disconnected.
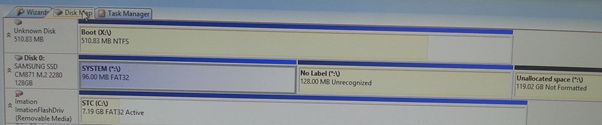
It seems the default VM created when you add a new Windows 2012 R2 server to the Telstra Cloud Shared infrastructure has a setting that enables RDP session disconnection after some idle period as all our VMs consistently exhibit this behaviour.
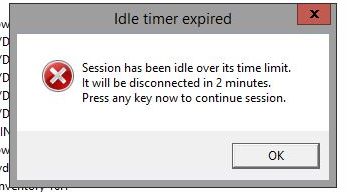
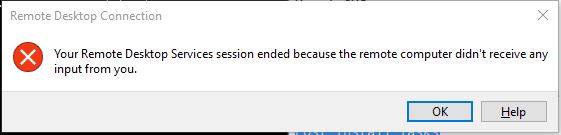
Below is what we would get in our RDP sessions after a few minutes of inactivity.
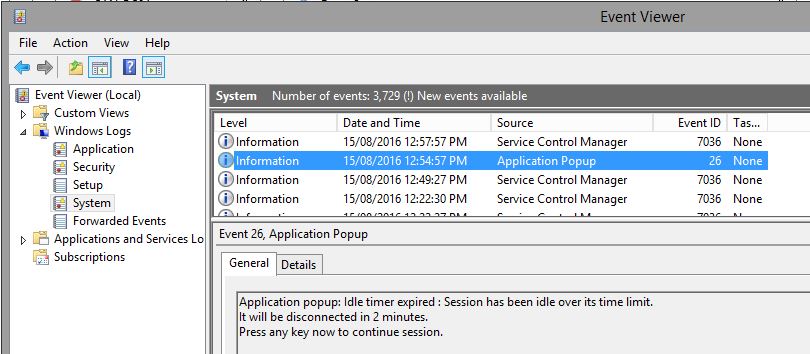
Session has been idle over its time limit. It will be disconnected in 2 minutes.
Your Remote Desktop Services Session ended because the remote computer didn’t receive any input from you.
This has annoyed our system admins as all their works and opened windows keep getting terminated that eventually we opened a ticket with Telstra Cloud support. However, after hours of troubleshooting and patiently waiting after every change of setting the problem was never really fixed.
What we’ve tried
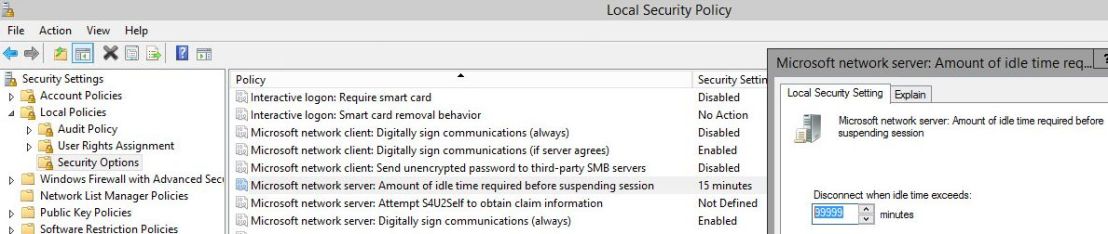
Opened Local Security Policy and went under Local Policies > Security Options > Microsoft network server: Amount of time required before suspending session. We changed this setting from the default 15 minutes and set it to the maximum value of 99999 (or 208 days). Unfortunately, this didn’t fix the problem.
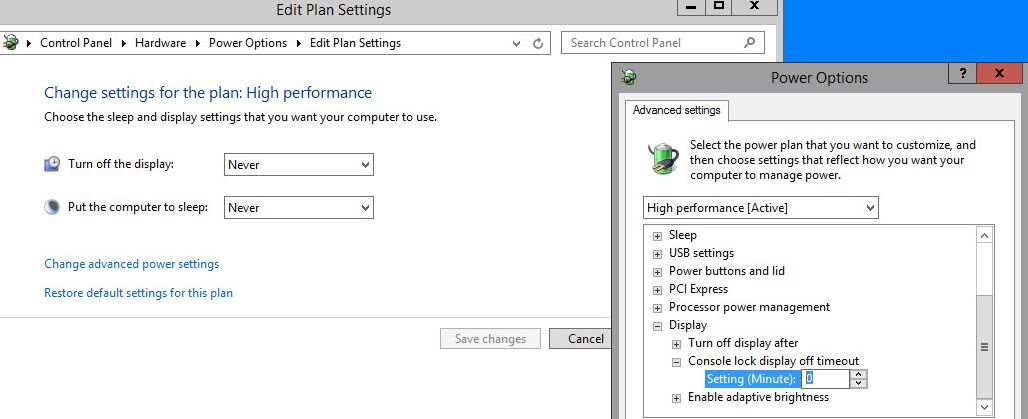
In our second attempt, we enabled the Console lock display off timeout setting in the Power Options via registry and set it to 0 (see this link). Again, this didn’t fix the problem.
Solution
I observed that around the time of disconnection the Event ID 26 below is logged in the System Event Viewer.
This behaviour happens since a policy setting enforces a time limit for idle Remote Desktop sessions.
What finally fixed it for us are the steps below.
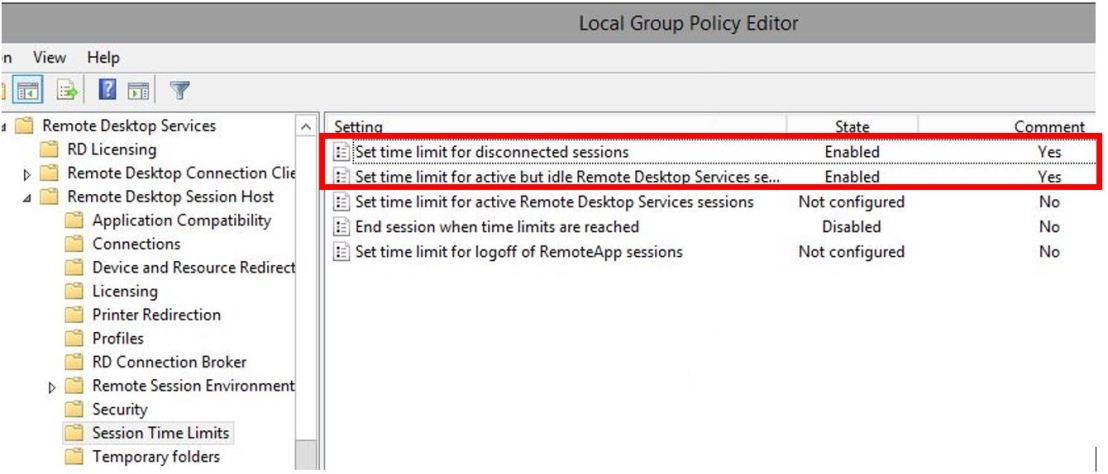
- In the Windows server, run gpedit.msc to open the Local Group Policy Editor
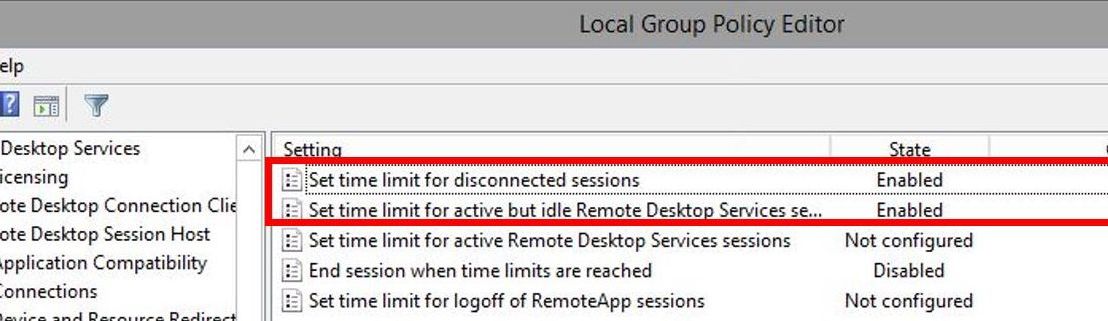
- Go to Computer Configuration > Administrative Template > Windows Components > Remote Desktop Services > Remote Desktop Session Host > Session Time Limits
- Set both entries highlighted below to Enabled and Never
Set time limit for disconnected sessions
Set time limit for active but idle Remote Desktop Services sessions
Hope this helps anyone who has been annoyed by this Windows behavior.